In an era of escalating digital threats, DevSecOps cybersecurity is vital for organizations aiming to safeguard their systems and data. By embedding security into every phase of the software development lifecycle, DevSecOps cybersecurity empowers teams to proactively identify cyber attacks, mitigate risks, and strengthen their security posture. This comprehensive guide delves into the core principles of DevSecOps cybersecurity, common attack vectors, detection strategies, and actionable steps to fortify your defenses.
Understanding DevSecOps Cybersecurity
DevSecOps cybersecurity integrates Development, Security, and Operations to create a collaborative framework where security is a shared responsibility. Unlike traditional models that treat security as an afterthought, DevSecOps cybersecurity embeds proactive measures into the development pipeline. This approach leverages automation, continuous monitoring, and cross-functional collaboration to deliver secure software faster while minimizing vulnerabilities.
Key components of DevSecOps cybersecurity include:
- Automation: Streamlines security testing and compliance checks.
- Collaboration: Aligns developers, security teams, and operations for unified goals.
- Continuous Integration/Continuous Deployment (CI/CD): Ensures security is part of every code release.
- Proactive Threat Mitigation: Identifies and addresses risks early in the development cycle.
Common Types of Cyber Attacks
To build a robust security posture, organizations must understand the cyber attacks threatening their systems. Here are the most prevalent threats:
- Phishing Attacks: Cybercriminals use deceptive emails, texts, or social media messages to steal credentials or install malware. Spear phishing targets specific individuals with tailored attacks.
- Malware: Includes ransomware (locks data until a ransom is paid), spyware (steals sensitive information), and trojans (disguise as legitimate software).
- Distributed Denial-of-Service (DDoS): Overwhelms servers with excessive traffic, disrupting services and causing downtime.
- SQL Injection: Exploits poorly secured databases to manipulate or extract sensitive data.
- Man-in-the-Middle (MitM) Attacks: Attackers intercept communications, such as unencrypted Wi-Fi connections, to steal data or impersonate users.
- Credential Stuffing: Uses stolen credentials to gain unauthorized access to accounts, exploiting password reuse.
- Zero-Day Exploits: Targets unpatched software vulnerabilities before vendors release fixes.
For a deeper dive into emerging threats, explore MITRE ATT&CK’s threat framework.
Identifying Cyber Attacks with DevSecOps Cybersecurity
DevSecOps cybersecurity equips organizations to detect and respond to cyber attacks swiftly. Key practices include:
- Threat Modeling: Analyze applications during the design phase to identify potential vulnerabilities and prioritize mitigation strategies. Tools like OWASP Threat Dragon assist in this process.
- Automated Security Scanning: Use Static Application Security Testing (SAST) to analyze source code and Dynamic Application Security Testing (DAST) to test running applications. Popular tools include SonarQube and Checkmarx.
- Continuous Monitoring: Deploy solutions like Splunk or Datadog to monitor real-time traffic, detect anomalies, and flag suspicious activities, such as unusual login patterns.
- Incident Response Automation: Implement Security Orchestration, Automation, and Response (SOAR) platforms like Palo Alto Networks Cortex XSOAR to automate alerts and accelerate incident response.
- Log Analysis: Use tools like Elastic Stack to analyze logs for signs of compromise, such as repeated failed login attempts or unauthorized API calls.
- Penetration Testing: Conduct regular simulated attacks to identify exploitable weaknesses in your systems.
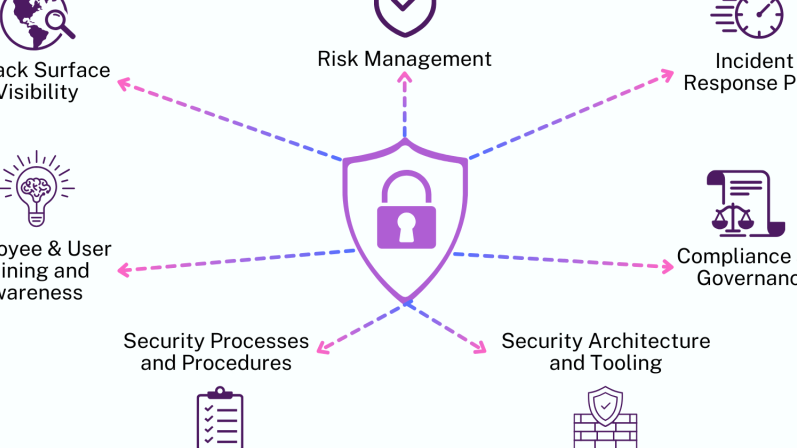
Strengthening Your Security Posture with DevSecOps
A resilient security posture requires proactive, layered defenses. DevSecOps cybersecurity offers proven strategies to enhance protection:
- Shift-Left Security: Integrate security at the earliest stages of development to identify vulnerabilities before code reaches production. Tools like Snyk help developers scan dependencies for vulnerabilities during coding.
- Secure Coding Practices: Train developers to follow guidelines from the OWASP Secure Coding Practices. This prevents common issues like cross-site scripting (XSS) or SQL injection.
- Patch Management: Maintain an inventory of software and apply patches promptly to address known vulnerabilities. Tools like Qualys automate patch deployment.
- Zero Trust Architecture: Adopt a “never trust, always verify” approach, requiring authentication for every user and device. Solutions like Okta support zero trust implementation.
- DevSecOps Tools: Leverage OWASP ZAP for automated vulnerability scanning, Trivy for container security, or HashiCorp Vault for secrets management.
- Employee Training: Conduct regular training on recognizing phishing emails, secure password practices, and social engineering tactics. Platforms like KnowBe4 offer comprehensive training modules.
- Secure CI/CD Pipelines: Integrate security checks into CI/CD workflows using tools like GitLab Security or Jenkins with security plugins.
- Backup and Recovery: Maintain encrypted backups and test disaster recovery plans to ensure business continuity post-attack.
Benefits of DevSecOps Cybersecurity
Implementing DevSecOps cybersecurity delivers measurable outcomes:
- Rapid Threat Detection: Automated scans and monitoring identify vulnerabilities in real-time.
- Cost Efficiency: Early vulnerability fixes reduce the financial impact of breaches, which can cost millions in fines and remediation.
- Enhanced Collaboration: Developers, security teams, and operations align on shared security goals.
- Regulatory Compliance: Automated checks ensure adherence to standards like GDPR, HIPAA, or PCI-DSS.
- Scalable Security: Adapts to new threats, ensuring long-term resilience.
- Improved Software Quality: Secure code enhances application performance and reliability.
Best Practices for Implementing DevSecOps Cybersecurity
To maximize the impact of DevSecOps cybersecurity, adopt these best practices:
- Automate Security Processes: Integrate tools like Snyk or Checkmarx into CI/CD pipelines for seamless vulnerability scanning.
- Foster a Security-First Culture: Encourage all teams to prioritize DevSecOps cybersecurity through regular training and clear policies.
- Conduct Regular Audits: Perform security audits and compliance checks to identify gaps and refine processes.
- Leverage AI and Machine Learning: Use AI-driven tools like Darktrace to predict and neutralize threats based on behavioral analysis.
- Stay Informed: Monitor emerging threats via resources like CISA’s Alerts and adapt strategies accordingly.
- Test Incident Response Plans: Conduct tabletop exercises to ensure teams are prepared for real-world attacks.
For additional guidance on secure development, refer to Snyk’s Secure Development Guide.
Conclusion
DevSecOps cybersecurity transforms how organizations identify cyber attacks and strengthen their security posture. By integrating security into development, automating detection, and fostering collaboration, businesses can counter threats effectively. Use tools like OWASP ZAP, SonarQube, and Snyk to identify cyber attacks and strengthen your defenses.
Call to Action: Embrace DevSecOps cybersecurity today. Leverage SonarQube or Snyk, train teams, and secure CI/CD pipelines to identify cyber attacks and strengthen your security posture. Act now!