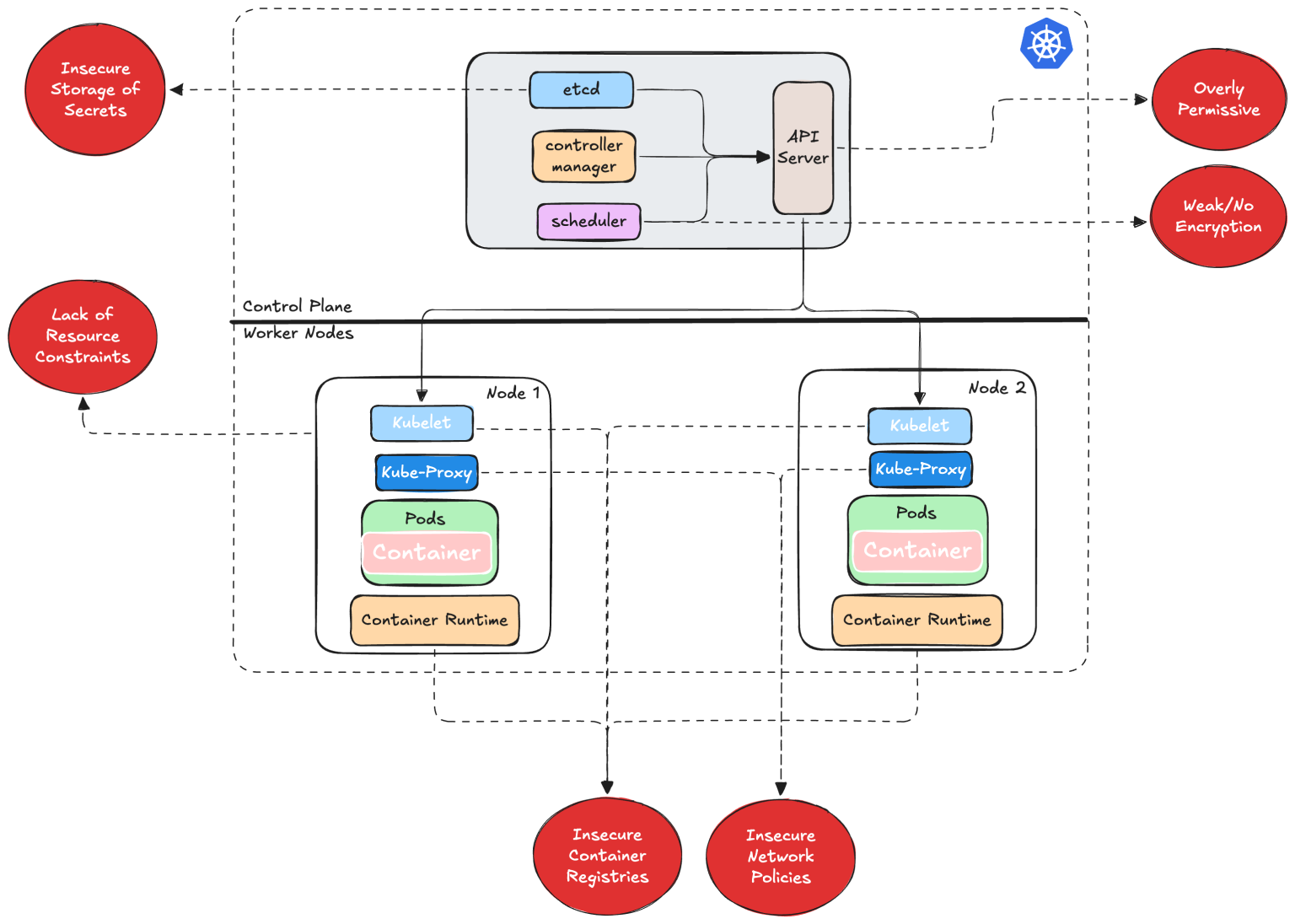
Kubernetes is the de facto platform for container orchestration, enabling scalable, resilient application deployment. However, Kubernetes security misconfigurations—errors in cluster configuration, access controls, or resource policies—can expose applications to cyberattacks, data breaches, and compliance violations. This comprehensive guide explores the nature of Kubernetes security misconfigurations, their causes, and seven detailed strategies to identify, remediate, and prevent them, ensuring secure Kubernetes clusters.
What Are Kubernetes Security Misconfigurations?
Kubernetes security misconfigurations are improper settings in Kubernetes clusters, workloads, or policies that create exploitable vulnerabilities. Common examples include:
- Overly permissive Role-Based Access Control (RBAC) roles.
- Containers running with root privileges.
- Exposed API servers or Kubernetes dashboards.
- Unrestricted network traffic between pods.
The consequences are severe:
- Data Breaches: Exposed APIs or storage volumes can leak sensitive data.
- Unauthorized Access: Weak RBAC may allow attackers to control clusters.
- Resource Abuse: Misconfigurations enable cryptojacking or denial-of-service attacks.
- Compliance Violations: Breaches may violate GDPR, HIPAA, or PCI-DSS.
A 2021 breach involving a misconfigured Kubernetes API server exposed customer data, highlighting the need for robust security. Learn more about Kubernetes security fundamentals in the Kubernetes documentation.
Why Do Kubernetes Misconfigurations Occur?
Kubernetes’ flexibility and complexity make it prone to errors. Key causes include:
- Limited Expertise: Teams new to Kubernetes may overlook security best practices.
- Default Configurations: Unchanged defaults, like permissive RBAC, introduce risks.
- Human Errors: Manual configuration mistakes create vulnerabilities.
- Lack of Monitoring: Without continuous scanning, misconfigurations go undetected.
- Deployment Pressure: Prioritizing speed over security leads to oversights.
7 Strategies to Address Kubernetes Security Misconfigurations
To achieve secure Kubernetes clusters, implement these seven strategies to fix and prevent Kubernetes misconfigurations.
1. Harden RBAC to Mitigate Kubernetes Misconfigurations
Overly permissive RBAC policies are a leading cause of Kubernetes security misconfigurations. To secure RBAC:
- Apply the principle of least privilege, granting only necessary permissions.
- Avoid broad roles like cluster-admin for non-critical tasks.
- Use Kube-bench to audit RBAC against the CIS Kubernetes Benchmark.
Example YAML:
yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: default
name: limited-access
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "list"]Action: Run kubectl get rolebindings,clusterrolebindings -A to review permissions and remove unnecessary access.
2. Prevent Root Containers for Secure Kubernetes Clusters
Running containers as root is a dangerous Kubernetes misconfiguration, allowing attackers to compromise the host. To mitigate:
- Set securityContext.runAsNonRoot: true in pod specs.
- Specify non-root user IDs (e.g., runAsUser: 1000).
- Scan for root containers with Falco, a runtime security tool.
Example YAML:
yaml
apiVersion: v1
kind: Pod
metadata:
name: secure-pod
spec:
containers:
- name: app
image: nginx
securityContext:
runAsNonRoot: true
runAsUser: 1000Action: Update pod manifests and verify with kubectl describe pod.
3. Secure the API Server to Fix Kubernetes Misconfigurations
An exposed API server is a critical vulnerability. To secure it:
- Enable TLS encryption for all API traffic.
- Disable anonymous authentication (–anonymous-auth=false).
- Restrict API access with network policies or firewalls.
Action: Audit API server settings with kubectl describe pod -n kube-system kube-apiserver. Refer to OWASP’s Kubernetes Security Cheat Sheet for best practices.
4. Enforce Network Policies to Avoid Misconfigurations
Unrestricted pod-to-pod traffic is a common Kubernetes misconfiguration. Network policies can:
- Limit ingress/egress traffic with specific rules.
- Apply policies to pods or namespaces using labels.
- Test policies with Kube-hunter.
Example YAML:
yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-all
namespace: default
spec:
podSelector: {}
policyTypes:
- Ingress
- EgressAction: Implement a deny-all policy and add allow rules for required traffic.
5. Protect Secrets Management for Secure Clusters
Mishandled secrets (e.g., API keys in plaintext) are a frequent vulnerability. To secure secrets:
- Use Kubernetes Secrets or external tools like HashiCorp Vault.
- Encrypt secrets at rest with encryptionConfiguration.
- Restrict access with RBAC.
Action: Enable encryption with kubectl apply -f encryption-config.yaml and audit secrets with kubectl get secrets -A.
6. Monitor Continuously to Detect Kubernetes Misconfigurations
Real-time monitoring catches vulnerabilities before exploitation. Use:
- Kube-bench for CIS compliance checks.
- Falco for runtime anomaly detection.
- Prometheus with Grafana for security metrics.
Action: Deploy a monitoring tool and configure alerts for misconfiguration events (e.g., unauthorized pod changes).
7. Automate Security to Prevent Cluster Misconfigurations
DevSecOps integrates security into CI/CD pipelines, reducing errors. Key practices:
- Scan YAML manifests with Checkov or Kube-score.
- Use Infrastructure as Code (IaC) with Terraform for consistent setups.
- Automate compliance checks for SOC 2 or NIST 800-53.
Action: Add a security scanner to your CI/CD pipeline (e.g., GitHub Actions) and enforce secure IaC templates.
Case Study: A Costly Kubernetes Misconfiguration
In 2022, a financial services company suffered a breach when a misconfigured Kubernetes dashboard was left publicly accessible. Attackers exploited it to deploy cryptojacking containers, costing $2 million in remediation and fines. Lessons learned:
- Disable unused dashboards (kubectl delete deployment kubernetes-dashboard -n kube-system).
- Implement network policies to restrict access.
- Deploy continuous monitoring to detect anomalies.
This breach could have been prevented with proper configuration and monitoring, emphasizing the need to address Kubernetes security misconfigurations.
Best Practices for Maintaining Secure Kubernetes Clusters
To ensure ongoing security:
- Update Regularly: Apply patches for vulnerabilities (e.g., CVE-2023-1234) using kubeadm upgrade.
- Audit Frequently: Conduct quarterly audits with CIS Benchmarks or Aqua Security’s Trivy.
- Train Teams: Educate DevOps on security via CNCF’s Kubernetes Security Training.
- Use Managed Services: Platforms like Amazon EKS or Google GKE offer built-in security features.
Tool Comparison: Kubernetes Security Solutions
| Tool | Purpose | Strengths | Best For |
|---|---|---|---|
| Kube-bench | CIS compliance auditing | Comprehensive, open-source | Initial audits, compliance |
| Falco | Runtime security monitoring | Real-time alerts, behavioral analysis | Runtime threat detection |
| Checkov | CI/CD manifest scanning | IaC support, broad integrations | DevSecOps pipelines |
| HashiCorp Vault | Secrets management | Enterprise-grade, multi-cloud | Secure secrets storage |
Conclusion
Kubernetes security misconfigurations are a significant threat, but proactive measures can mitigate risks. By hardening RBAC, securing APIs, enforcing network policies, and adopting DevSecOps, you can achieve secure Kubernetes clusters. Continuous monitoring and automation further strengthen defenses, protecting your applications from breaches.
Take action now: Download our free Kubernetes Security Checklist or contact us for a demo of our advanced monitoring platform to address Kubernetes misconfigurations.